Part 3 -- The Disconnect Between Theory And Practice
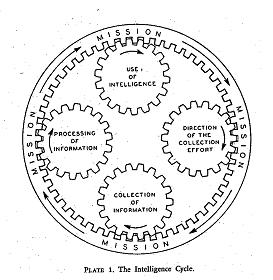
 Finding descriptions of the intelligence cycle is not difficult. Virtually every organization, company or law enforcement agency that has even a modest intelligence capability has a picture, much like the one to the right (which, until recently, graced the US national security intelligence community’s main web site, Intelligence.gov).
Finding descriptions of the intelligence cycle is not difficult. Virtually every organization, company or law enforcement agency that has even a modest intelligence capability has a picture, much like the one to the right (which, until recently, graced the US national security intelligence community’s main web site, Intelligence.gov). So pervasive is this traditional image of the intelligence process that it comes across as generally accepted theory. Indeed, many private sector practitioners have built much of their marketing campaigns on touting the benefits of the cycle.
Likewise, it is commonplace to see the cycle featured prominently in government publications, statements of doctrine, training publications and even in critiques of intelligence. The entire architecture of intelligence, across all three major sub-disciplines of intelligence, is caught up in this more or less common vision of how intelligence professionals perform the functions of intelligence.
Despite its popularity, the history of the cycle is unclear. US army regulations published during WWI identify collection, collation and dissemination of military intelligence as essential duties of what was then called the Military Intelligence Division (Fun fact: According to Congressional testimony in 1919 the whole budget for military intelligence in 1913 was $10,000 -- or roughly $227,000 in 2011 dollars) but there was no suggestion that these three functions happen in a sequence, much less in a cycle.
By 1926, military intellgence officers were recommending four distinct functions for tactical combat intelligence: Requirements, collection, "utilization" (i.e. analysis), and dissemination, though, again, there was no explicit mention of an intelligence cycle.
The first direct mention of the intelligence cycle (see image to the right) I could find is from the 1948 book, Intelligence Is For Commanders (more on this book here). I hypothesize that the intelligence cycle probably came into use during WWII as a training aid but I have not been able to find any evidence to corroborate this bit of speculation on my part.
Since that time, the cycle, as a model of how intelligence works, has become pervasive. A simple Google image search on the term, "Intelligence Cycle" rapidly gives one a sense of the wide variety of agencies, organizations and businesses that use some variant of the cycle.
(Note: Experienced intelligence professionals might want to skip the next few paragraphs, which outline a more or less generic version of the intelligence cycle based on the image at the top of the post. I include it here for readers who are not familiar with the cycle or for students of intelligence who might need a refresher.)While the actual details vary dramatically (something we will turn to in the next post) in a typical description of the process, the intelligence cycle usually begins with planning and direction or similar language. Direction usually comes from the decisionmakers that the intelligence activity supports although it can also come from the senior leaders of the intelligence activity or even from the analysts themselves.
It is important to note here that direction and planning can be formal but is often done informally (most variants of the cycle make no distinction). This is seen most often when there is no time for a more formal process. Less formal tasking is also often seen in smaller intelligence units, such as in business environments, or in units where the intelligence professionals and decisionmakers have a long-term relationship.
After the planning and direction phase, the collection phase, in a typical version of the intelligence cycle, begins. Here the intelligence professional begins to execute the plan to collect the types of information necessary to understand and answer the requirement.
Once the intelligence unit collects the information necessary, other intelligence professionals within the same unit might have to process and exploit it. Processing and exploitation takes on a number of forms including decrypting encrypted transmissions, turning a variety of conversations into a single cohesive report, translating source information from one language into another or identifying buildings and other features in an aerial image, among others. In short, processing and exploitation is the phase where very raw information becomes usable to the largest number of people authorized to view it within the intelligence organization.
With planning, direction, collection, exploitation and processing complete, the focus of the traditional intelligence cycle shifts to analysis and production, or the interpretation of the collected data and the creation of a product that best meets the decisionmaker’s needs.
Analysts need the widest possible variety of information sources in order to be able to corroborate other information and to answer the requirement with which they are dealing. The notional source of the information is much less important than its relevance to the requirement at hand and that source’s reliability.
Production carries its own concerns and they are often independent of the analysis. If the analyst is concerned with the content of the analysis, the intelligence production specialist is concerned with its form. Appropriate forms, in turn, depend on the needs and desires of the decisionmaker the intelligence unit supports. For example, while the traditional intelligence product within many areas of the US national security community is a written document with a smattering of pictures and graphs to explain key points, business decisionmakers tend to be much more comfortable with charts, graphs, and numerical data accompanied by a few explanatory bullets.
The final phase according to the diagram is dissemination. This is where the intelligence specialist delivers the final product to the decisionmaker. While this sounds fairly easy, it, too, has a number of pitfalls associated with it. Questions concerning exactly to whom an intelligence document should go to and exactly how it should get there are fundamental to this phase. For example, classification, or the level of secrecy or confidentiality associated with the intelligence product, is one such issue.
Likewise, many people in developed countries take high-speed voice and data communications capabilities for granted. Yet, in many cases, particularly in intelligence work, such capabilities are scarce or degraded due to geographic isolation. In these cases, the bandwidth available may determine where the intelligence product is sent or even if it is sent via electronic means at all.
Next: Critiques Of The Cycle





No comments:
Post a Comment